We support major blockchain ecosystems and Blockchain programming languages. Below outlines our auditing methodology and highlights key auditing features.
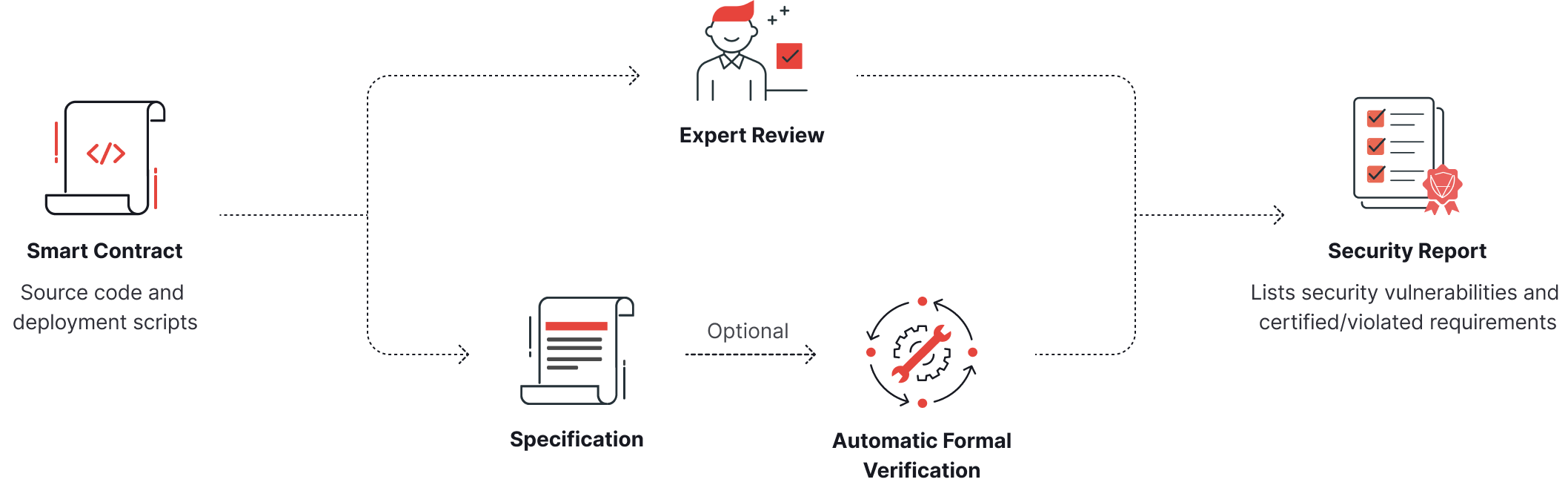
Audit Process
Our audit process follows the following steps:
1. Environment Setup: Pre-configured VM environments simplify setup and enable auditors to run code and tests for hands-on project understanding.
2. Architecture Review: Assessing security-critical components, interactions, external input handling, library imports, novel implementations, code standard compliance, and concurrency usage.
3. Threat Modeling: Establishing security requirements based on system architecture, creating a security checklist for thorough evaluation.
4. Static Analysis and Formal Verification: Leveraging a suite of tools with a vast database of 60,000+ findings from 4,000+ audits, testing code statically, and using formal verification to ensure program correctness.
5. Manual Review: Meticulous line-by-line code examination, including micro-auditing for individual function understanding and macro-auditing for global vulnerability identification.
6. Reporting and Remediation: Detailed audit reports with findings and recommendations, followed by an ongoing dialogue with clients for iterative security improvements until satisfaction is achieved.
Environment Setup
While some languages and projects may require a complicated setup process, this issue is mitigated through the use of pre-configured virtual machine environments. Code added to the environment will be checked for successful compilation and deployment capabilities. The environment enables auditors to run code and perform tests to gain hands-on understanding of the project.
Architecture Review
Determining the project architecture is crucial for understanding the security-critical components and parts of the system. Architecture extraction involves examining the interactions between components, the handling of external inputs, the import of libraries, the implementation of novel ideas, compliance with code standards, and the usage of concurrency. It is also important to determine if a project is an original design or a fork of another project. Forks may inherit vulnerabilities from the original project.
Threat Modeling
A Threat Model is a representation of a system that includes a description of its critical assets, resources, and security requirements, as well as a list of its potential vulnerabilities and possible security threats. The abstract description is established during the architecture review, and the security requirements can be determined by posing and answering questions about the system based on its architecture.
Once the security requirements have been established, it's time to consider the possible threats.The outcome of the Threat Modeling process produces a security checklist that guides the security audit and ensures a thorough evaluation of the system's security posture.
Static Analysis and Formal Verification
We leverage our extensive experience and longevity through our suite of tools, which utilize a vast database of over 60,000 previous findings from more than 4,000 completed audits and identified incidents. Tools test code statically, at both the source code and bytecode levels, and are capable of identifying insecure code patterns and generating diagrams to provide insight into the Blockchains. The tools improve as our database of findings grows with each audited project.
In addition to static analysis by tools, we secure client code through formal verification, ensuring that the program meets its desired specifications. Formal verification is a mathematical method of proving that a computer program functions as intended. It involves expressing the program's properties and expected behavior as mathematical formulas, and then using automated tools to check that these formulas are true. Key findings from the tools encompass logic issues, reentrancy risks, lack of access controls, overflow/underflow, and gas optimization, among others. The findings generated by the tools are subjected to manual verification by auditors to eliminate false positives and enhance the clarity of the results.
Manual Review
Manual review involves a meticulous line-by-line examination of the code and is the most time-intensive step in the procedure. The manual review can be divided into two parts: micro-auditing and macro-auditing. Micro-auditing involves analyzing code to understand each function, and this process often reveals bugs. Techniques for micro-auditing include analyzing each argument, variable, and field, reviewing function access levels and state field modifications, and comparing similar functions. On the other hand, macro-auditing involves identifying global vulnerabilities by understanding the project's call/contract hierarchy, searching for state field and function occurrences, and checking different what-if conditions. High impact vulnerabilities are often not limited to a single function, but may result from incorrect interactions among multiple functions located in different parts of the code.
Reporting and Remediation
Our audit reports provide a detailed analysis of a project's security posture, starting with an overview of the project's type, ecosystem, and scope. The reports explain our methodology and the auditing approach used to evaluate the project's security.
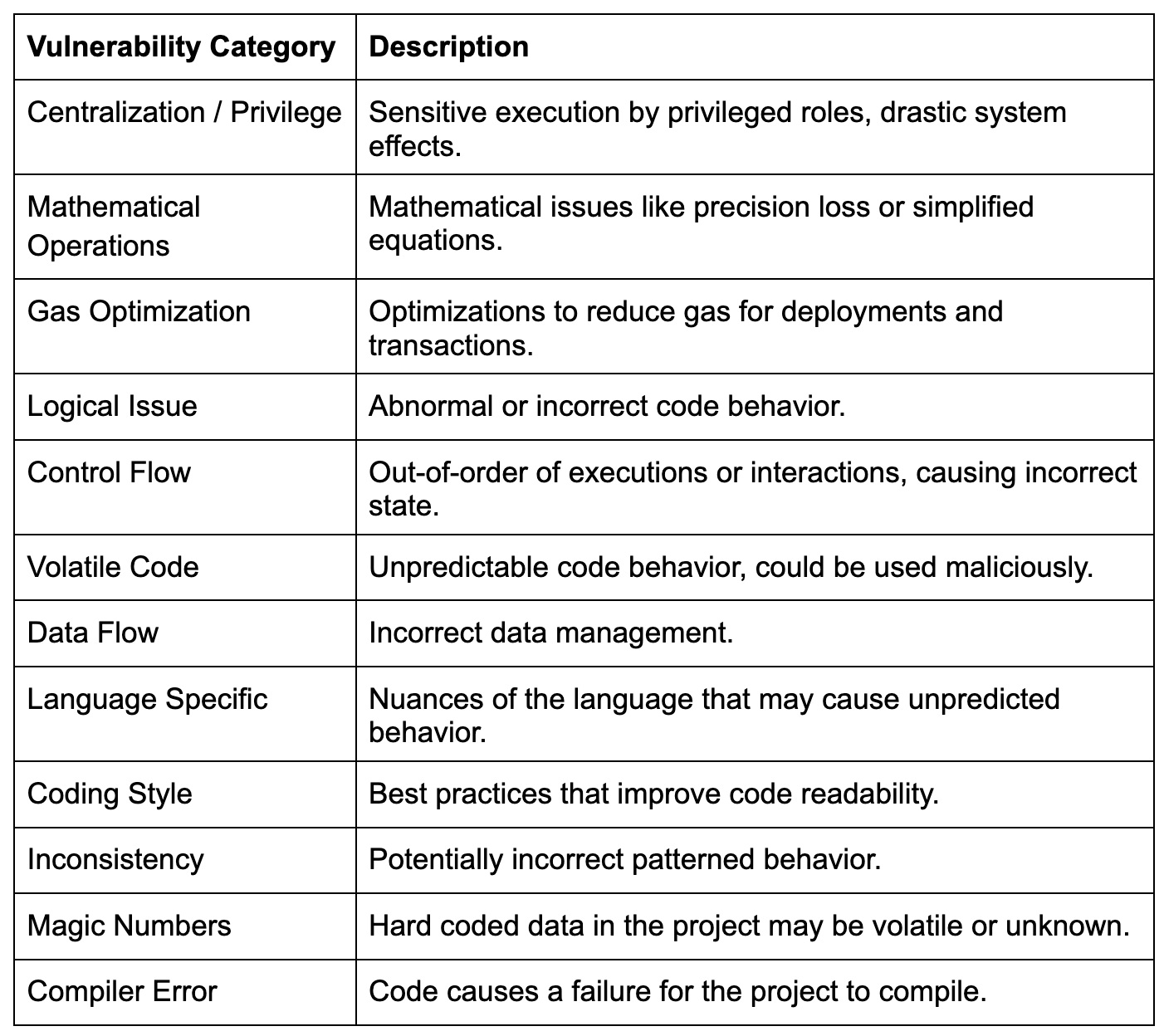
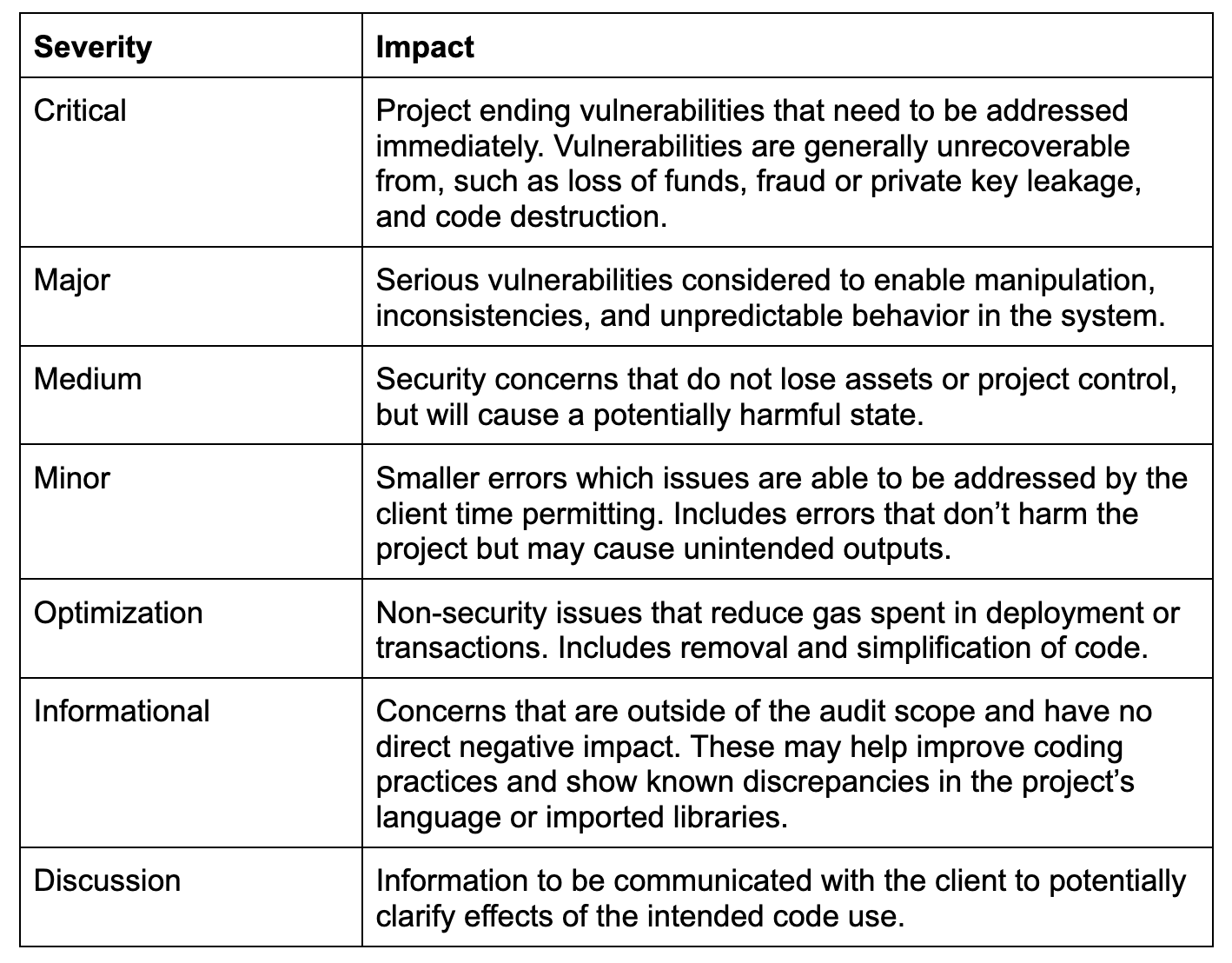
The findings we provide include detailed explanations that identify, categorize, and provide recommendations for the issues found in a project. Each finding includes a title and metadata such as the category, severity, file location and alleviation status. Four distinct written sections accurately detail security considerations.
The remediation phase is an ongoing dialogue between the client and auditors that aims to further improve the security of a project. The initial security assessment is provided to the client, who then responds with updated source code or comments. The findings are subsequently updated to reflect any changes made to the code and are published in an updated report. This process repeats until the client is satisfied with the final security assessment. The report is published to clients and publicly available on the Security Leaderboard where community members can view how projects are improving their security rating using CertiK audits and security services.
 Explore Certified Kernel Tech LLC's Store
Visit Certified Kernel Tech LLC's shop to find a range of tailored products that can enhance your experience and meet your needs.
Explore Certified Kernel Tech LLC's Store
Visit Certified Kernel Tech LLC's shop to find a range of tailored products that can enhance your experience and meet your needs.



